SOLUTIONS
Customer Security
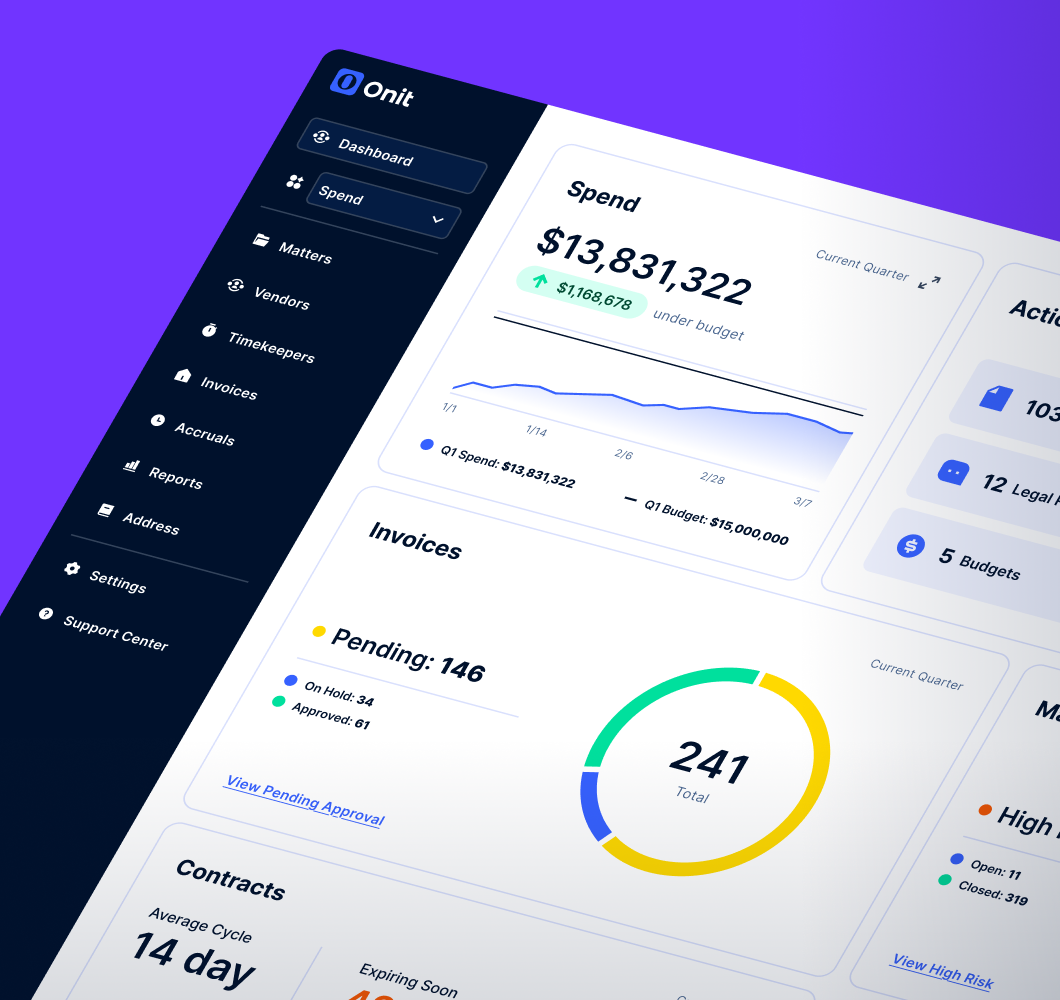
Our priority is protection
With state-of-the-art technology to ensure your data is protected, collaborating on projects securely (with access for only authorized participants) has never been easier.
A cutting-edge approach to security
Our data is secured using bank-grade 256-bit Secure Sockets Layer (SSL) encryption and is stored in an enterprise-class, secured hosting environment that is backed up daily. All data within Onit remains the property of the project owner and cannot be accessed by any other user.
Key Specifications
Physical security measures include a SSAE-18 Type II SOC II datacenter, dedicated servers, redundant power connections with standby generators, multiple redundant network connections, biometric scanning for controlled data access, and 24/7 video monitoring. Physical security is audited by an independent firm.
Key Specifications
Custom-hardened Unix kernels, Managed virtual private cloud, Managed continuous firewall monitoring, Policies and Procedures. By policy, employees are prohibited from accessing private data; Onit claims no ownership of your data. 24/7 monitoring and escalation. All users must be verified by email.
Key Specifications
System installation using hardened, patched OS System patching configured to provide ongoing protection from exploits. Dedicated firewall and VPN services to help block unauthorized system access. Data protection with managed backup solutions. Distributed Denial of Service (DDoS) mitigation services
Key Specifications
Onit audits to SSAE-18 SOC 2 Type 2, SOC 1 Type 2 and HIPAA standards, verified by an independent auditing firm. Encryption for all administrative traffic (HTTPS, SFTP, SSH). Encryption for all customer traffic (HTTPS). Datacenter employees trained on documented Systems access logged and tracked for auditing purposes Secure document-destruction policies for all sensitive information Fully documented change-management procedures Independently audited disaster recovery and business continuity plans
Get a demo
Ready to get started?
Contact our team who can design a custom solution for your business.